PowerShell Remoting is a very powerful tool for each administrator, as it enables remote management of Windows Servers and Clients through PowerShell.
On Windows Server 2016 and Windows Server 2012 R2, PowerShell Remoting is enabled by default. However, in previous versions as well as in client versions of Windows, you will need to enable it by yourself. Since it is not wise to log on to each server and use the Enable-PSRemoting cmdlet interactively, we will use Group Policy to do it for us.
Since there is no specific policy to enable PowerShell Remoting, we will need to configure each parameter required to work properly. This means that we will create HTTP(S) Listeners, configure automatic start of the WinRM service and the set the appropriate rules in the Windows Firewall.
Enable PowerShell Remoting using Group Policy
First, open the Group Policy Management Console window and create a new Group Policy Object. You do not need to apply it to an OU yet, it would be better to test it before dropping it into production servers.
Configure WinRM Listeners
Follow the path: Computer Configuration \ Administrative Templates \ Windows Components \ Windows Remote Management (WinRM) \ WinRM Service
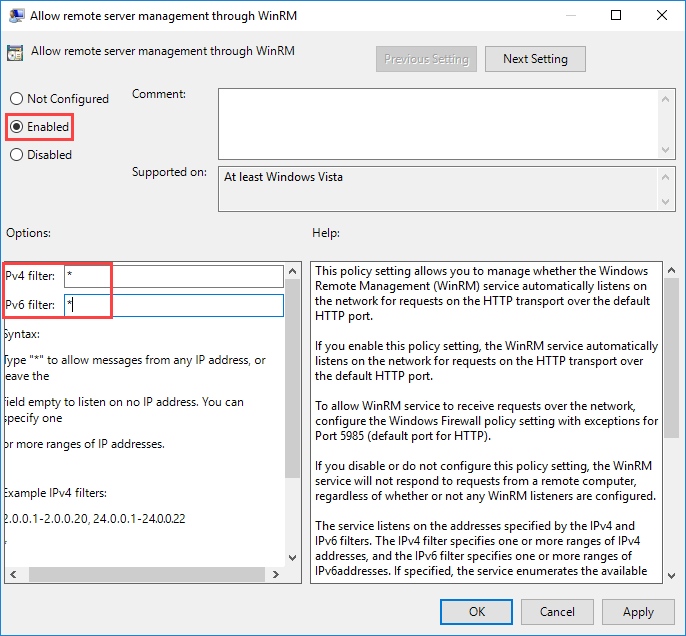
Here, open Allow remote server management via WinRM and set the switch to Enabled. In the filter field, use the wildcard (*) to specify all IP addresses or use a specific IP address range for greater security and server lockdown.
Set the WinRM service to start automatically
WinRM service runs automatically, by default, in the latest versions of Windows Server. However, this is not the case with Windows client computers. So, you can start the service through Group Policy. Let me point out that Group Policy will start the WinRM service on the next computer restart as it can not be done dynamically at any given time.
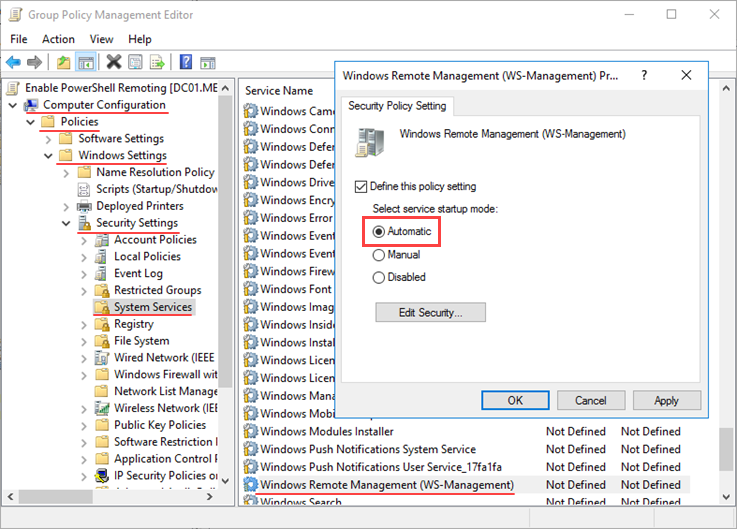
Follow the path: Computer Configuration \ Windows Settings \ Security Settings \ System Services
Here, double-click Windows Remote Management (WS-Management) to see its properties and set the start-up mode to Automatic, as shown in the figure below.
Configure Windows Firewall
Follow the path: Computer Configuration \ Policies \ Windows Settings \ Security Settings \ Windows Firewall with Advanced Security
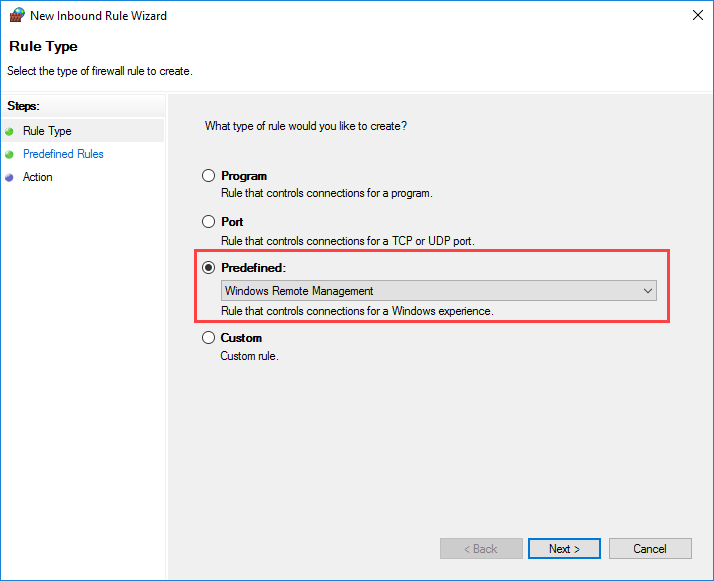
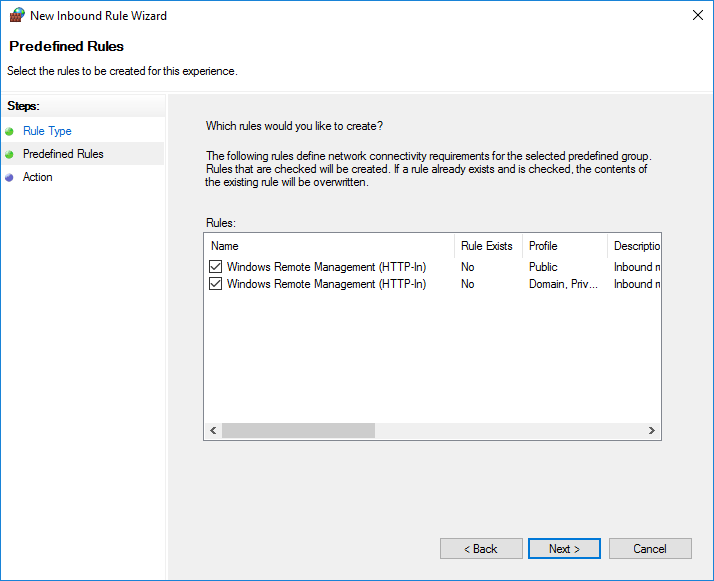
Here, right-click on Inbound Rules and then in New Rule. In the window that appears, enable the Predefined type and select Windows Remote Management.
Choose whether to allow access to Domain / Private networks and/or Public networks.
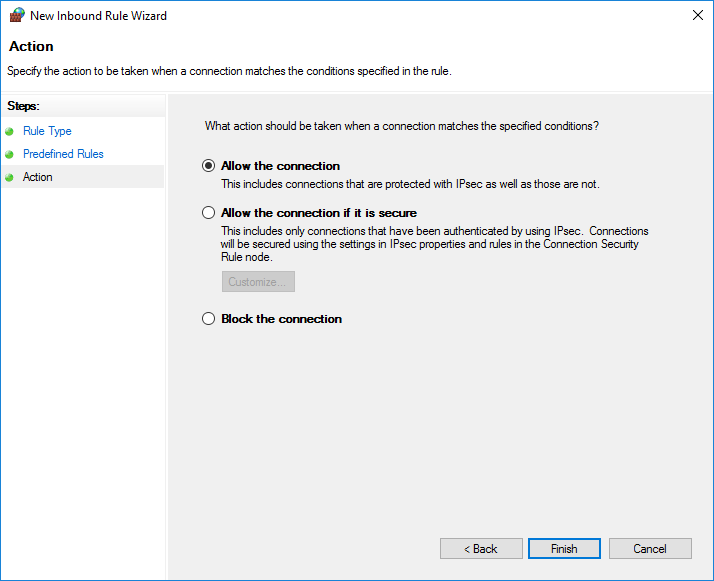
Finally, leave Allow the connection enabled and click Finish to create the new rules in the Windows Firewall.
That’s it!




I’m not in a domain environment. I can allow WinRM and set the firewall rules by local policy, but I don’t see a way via local policies to guarantee a service startup. Any suggestions?
just go to services and rightclick on the winrm service and set the service to automatic startup.
Or run this as admin:
Get-Service -Name “winrm” | Set-Service -StartupType Automatic