Remote management of Windows Server 2016 is enabled by default, but Remote Desktop, on the other hand, is disabled. So, you have to turn it on in order to access a Windows Server remotely.
Depending on the case, we can enable the Remote Desktop directly using the graphical user interface, PowerShell or by implementing the appropriate policies through Group Policy.
Note: In Windows Server 2016 Essentials, Remote Desktop is enabled by default.
Enable Remote Desktop using the GUI
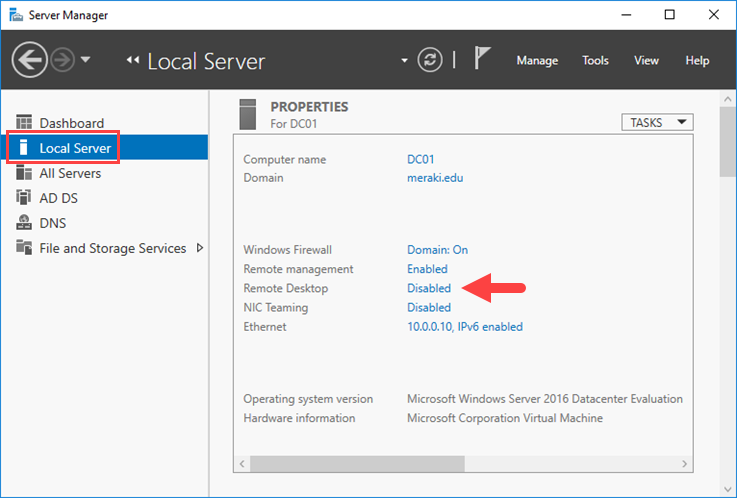
Open Server Manager and click Local Server from the left pane. Here, click Disable in the Remote Desktop field.
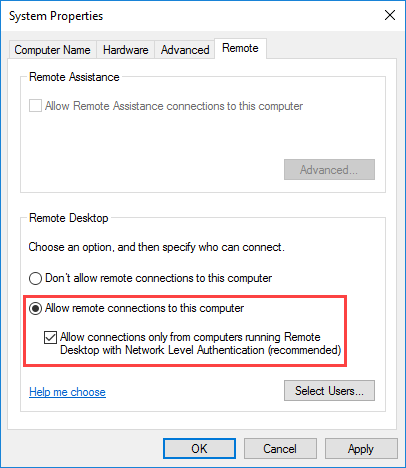
In the window that appears, enable the Allow remote connections to this computer setting. At this point, you can choose whether to allow NLA connections by enabling the corresponding setting but also to select which additional users or groups to connect other than administrators.
Once you’ve enabled the above setting, you’ll see a message to enable the corresponding Windows Firewall rule that will allow Remote Desktop Connection from any source address.
That’s it! Once you upgrade to Server Manager, you will see that the Remote Desktop setting has changed to Enabled.
Enable Remote Desktop using PowerShell
To enable Remote Desktop through PowerShell, you will need to add two keys to the registry and a rule in the Windows Firewall. Commands should run in a PowerShell window with administrator privileges.
By running the following command, the Remote Desktop will be enabled, allowing connections via Terminal Services.
New-ItemProperty -Path 'HKLM:\System\CurrentControlSet\Control\Terminal Server\' - Name "fDenyTSConnections" -Value 0 -PropertyType dword -Force |
By running the following command, the predefined Windows Firewall rules will be activated for the Remote Desktop on all profiles.
Enable-NetFirewallRule -DisplayGroup "Remote Desktop" |
Finally, the following command enables Network Level Authentication (NLA) for Remote Desktop connections.
New-ItemProperty -Path 'HKLM:\System\CurrentControlSet\Control\Terminal Server\WinStations\RDP-Tcp\' -Name "UserAuthentication" -Value 1 -PropertyType dword -Force |
Enable Remote Desktop using Group Policy
To enable Remote Desktop Connection, follow the path below and set the Allow users to connect remotely using Remote Desktop Services to Enabled.
Computer Configuration \ Policies \ Administrative Templates \ Remote Desktop Services \ Remote Desktop Session Host \ Connections
To enable user authentication through Network Level Authentication (NLA), follow the path below and set the Require Network User Authentication policy to Enabled.
Computer Configuration \ Policies \ Administrative Templates \ Remote Desktop Services \ Remote Desktop Session Host \ Security
To enable the rules in the Windows Firewall, follow the path below and set the policy Windows Firewall: Allow inbound Remote Desktop exceptions to Enabled.
Computer Configuration \ Policies \ Administrative Templates \ Network \ Network Connections \ Windows Firewall \ Domain Profile
These were the three basic methods to enable Remote Desktop connections in Windows Server 2016. Of course, depending on your business security level, you may need to go ahead with further settings for who can access and from where.